As part of a comprehensive cybersecurity posture, utilities must incorporate solutions that acknowledge the fact that in many cases, existing resources are limited, whether they be financial, human or technical. Simple, easy to manage and cost-effective security solutions that do not require on-site cyber security expertise are essential to any utility seeking to mitigate risk. These solutions must be able to protect critical infrastructure and in the event of an attack, also be able to straightforwardly and quickly identify assets under attack and easily explain what steps should be taken to mitigate such attack BEFORE any damage is done.
As part of a comprehensive cybersecurity posture, utilities must incorporate solutions that acknowledge the fact that in many cases, existing resources are limited, whether they be financial, human or technical. Simple, easy to manage and cost-effective security solutions that do not require on-site cyber security expertise are essential to any utility seeking to mitigate risk. These solutions must be able to protect critical infrastructure and in the event of an attack, also be able to straightforwardly and quickly identify assets under attack and easily explain what steps should be taken to mitigate such attack BEFORE any damage is done.

Lorem Ipsum is simply dummy text of the printing and typesetting industry. Lorem Ipsum has been the industry's standard dummy text ever since the 1500s, when dummy text ever since the 1500s, whendummy text ever since the 1500s, when dummy text ever since the 1500s, whendummy text ever since the 1500s, when dummy text ever since the 1500s, whendummy text ever since the 1500s, when

Lorem Ipsum is simply dummy text of the printing and typesetting industry. Lorem Ipsum has been the industry's standard dummy text ever since the 1500s, when dummy text ever since the 1500s, whendummy text ever since the 1500s, when dummy text ever since the 1500s, whendummy text ever since the 1500s, when dummy text ever since the 1500s, whendummy text ever since the 1500s, when

Lorem Ipsum is simply dummy text of the printing and typesetting industry. Lorem when dummy text ever since the 1500s, whendummy text ever since the 1500s, when when dummy text ever since the 1500s, whendummy text ever since the 1500s, when

Lorem Ipsum is simply dummy text of the printing and typesetting industry. Lorem Ipsum has been the industry's standard dummy text ever since the 1500s, when dummy text ever since the 1500s, whendummy text ever since the 1500s, when dummy text ever since the 1500s, whendummy text ever since the 1500s, when dummy text ever since the 1500s, whendummy text ever since the 1500s, when
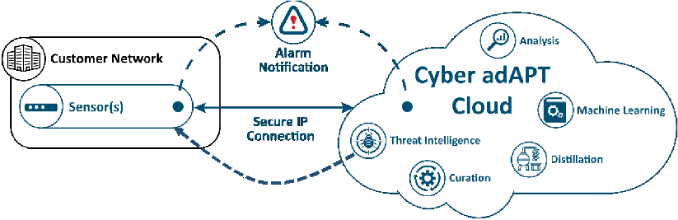
HydroPro has partnered with Cyber adAPT to deliver a network threat detection solution specially optimized for the water and wastewater sector. This solution passively monitors all network traffic within the public utility 24/7 looking for active cyber threats as they start to penetrate the network. When a cyber-attack is identified, the system immediately alerts the utility and public entities and provides clear, easy to understand steps on how to mitigate the threat. The solution is simple to install, requires no active maintenance and automatically updates itself with the latest threat intelligence. Combining on-site network detection with cloud-based machine learning and artificial intelligence, the system significantly improves any existing cybersecurity posture by providing critical protection from cyber attacks in real time.






Contact HydroPro Solutions today to learn more about how HydroPro NTD can protect your infrastructure and to schedule a free trial.
HydroPro Solutions | (512) 940-5980
www.hydroprosolutions.com | [email protected]